The Cybersecurity Maturity Model Certification (CMMC), announced in January 2020, requires U.S. Department of Defense contractors to achieve one of five baseline security levels. The model is a stepped approach that includes 17 domains with a number of security best processes and practices within each domain. The incremental approach allows organizations to improve their cybersecurity posture over time. It is very similar to moving upwards in levels in gaming. The five levels include:
| Processes | Number of Processes | Practices | Number of Practices | |
| LEVEL 1 | Performed | 0 | Basic | 17 |
| LEVEL 2 | Documented | +2 (2 total) | Intermediate | +55 (72 total) |
| LEVEL 3 | Managed | +1 (3 total) | Good | +58 (130 total) |
| LEVEL 4 | Reviewed | +1 (4 total) | Proactive | +26 (156 total) |
| LEVEL 5 | Optimized | +1 (5 total) | Advanced/Progressive | +15 (171 total) |
While there is no deadline for CMMC compliance, it will be incorporated as a requirement into new DoD contract request for proposals (RFPs), which will specify the required certification level to participate in various projects.
As organizations rush to comply with the new CMMC, what does it take to get on the playing board with Level 1 certification?
Processes. There are no required formal processes for CMMC Level 1. Select practices are documented where required.
Practices. There are 17 required practices for CMMC Level 1. They span 6 of the 17 domains and are equivalent to all practices in Federal Acquisition Regulation (FAR) 48 CRF 52.204-21.
| AC.1.001 | Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems). |
| AC.1.002 | Limit information system access to the types of transactions and functions that authorized users are permitted to execute. |
| AC.1.003 | Verify and control/limit connections to and use of external information systems. |
| AC.1.004 | Control information posted or processed on publicly accessible information systems. |
| IA.1.076 | Identify information system users, processes acting on behalf of users, or devices. |
| IA.1.077 | Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational information systems. |
| MP.1.118 | Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse. |
| PE.1.131 | Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals. |
| PE.1.132 | Escort visitors and monitor visitor activity. |
| PE.1.133 | Maintain audit logs of physical access. |
| PE.1.134 | Control and manage physical access devices. |
| SC.1.175 | Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems. |
| SC.1.176 | Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks. |
| SI.1.210 | Identify, report, and correct information and information system flaws in a timely manner. |
| SI.1.211 | Provide protection from malicious code at appropriate locations within organizational information systems. |
| SI.1.212 | Update malicious code protection mechanisms when new releases are available. |
| SI.1.213 | Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed. |
Many organizations likely already implement the basic security best practices required for CMMC Level 1, and filling in any gaps should be easily achieved.
Leveling up to intermediate CMMC Level 2 requires documenting all Level 1 practices, creating a policy that includes all activities, and 55 additional practices that align with NIST SP800-171r1 Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.
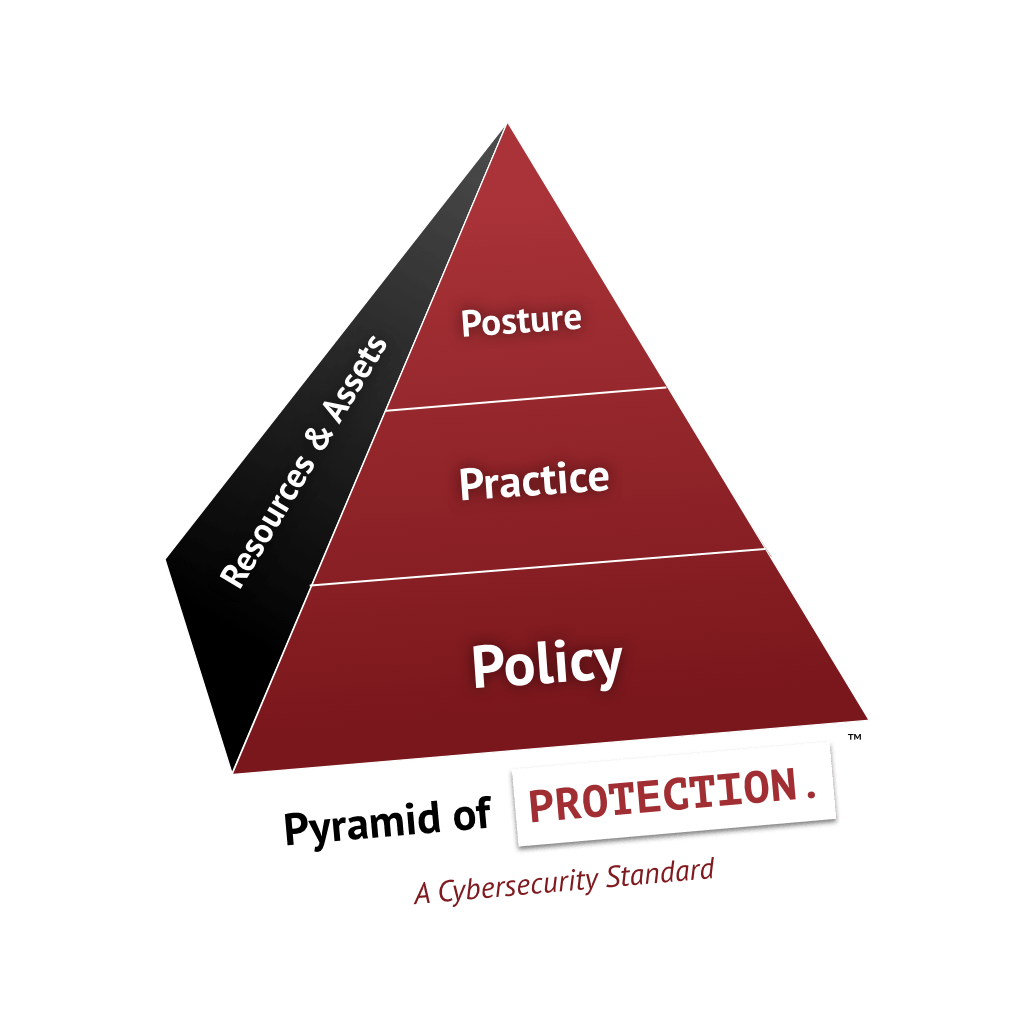
SHINE System’s Pyramid of Protection helps organization’s meet regulatory requirements across people, processes, and technology. The Pyramid of Protection addresses regulatory requirements like CMMC by ensuring strong cybersecurity protections across the areas of policy, practice, and posture.
Pursing the new CMMC requirements may take some effort, especially leveling up to higher levels, but the requirements will strengthen an organization’s security posture. The CMMC is a game worth playing, so get on the board and start leveling up.
Pursing the new CMMC requirements may take some effort, especially leveling up to higher levels, but the requirements will strengthen an organization’s security posture. The CMMC is a game worth playing, so get on the board and start leveling up.
Cyber disruptions are increasing in such frequency and severity that it’s no longer a matter of “if” but instead a matter of “when.” Organizations need to prepare. Vulnerabilities lead to erosion of confidentiality, integrity, or availability that may stem from malicious attacks, accidents, or natural occurrences.
SHINE Systems helps customers establish cyber resilience, enabling them to operate in the face of these threats through proactive prevention and detection, streamlined response, and rapid recovery.
For more information on our Cybersecurity services, please call Dr. Angela Orebaugh at 434-322-3000 Ext. 102 or email cyber@SHINESystems.com.
About the Author
Angela Orebaugh, Ph.D. is a technologist, educator, researcher, and author with a broad spectrum of expertise in information technology and security. She synergizes her 20 years of hands-on strategic and technical experiences within industry, academia, and government to advise clients on information technology and security strategy, management, and technologies.

