Cybersecurity
One Mission.
One Team.
We deliver analysis, cybersecurity, mission support, and technology solutions to create a strategic and tactical advantage wherever the mission takes us.
For over a decade, we have delivered expertise and timely information to empower our federal customers’ decisive action.
We are partners in your mission.
Cybersecurity
Cyber disruptions are increasing in such frequency and severity that it’s no longer a matter of “if” but instead a matter of “when”.
Organizations need to prepare. Vulnerabilities lead to erosion of confidentiality, integrity, or availability that may stem from malicious attacks, accidents, or natural occurrences.
We help customers establish cyber resilience, enabling them to operate in the face of these threats through proactive prevention and detection, streamlined response, and rapid recovery.
Pyramid of Protection™
SHINE System’s Pyramid of Protection helps organizations ensure cyber resilience through policy, practice, and posture across all resources and assets.
For more information on our Cybersecurity services, please email cyber@SHINESystems.com.
SHINE Systems can help you:
- Protect your organization with proactive policy, practice, and posture
- Reduce the financial impact of cyber disruptions
- Meet regulatory requirements
- Improve internal processes
- Protect brand and reputation
- Strengthen customer trust
- NIST Cybersecurity Framework (CSF) compliant
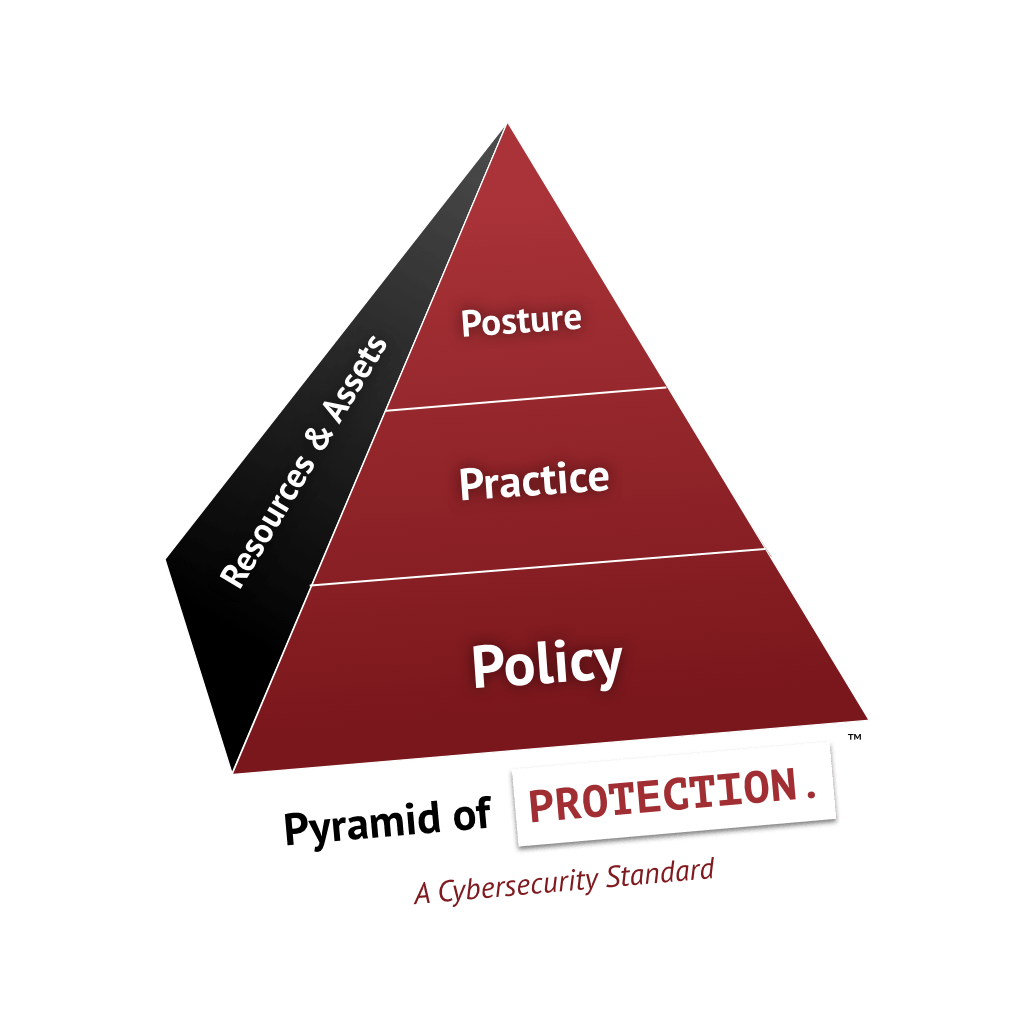
Policy
Ensure leadership support
Develop a culture of security
Develop a cybersecurity management program
Identify and classify critical data
Identify and assess risk
Develop security policies
Create IRP/BCP/DRP
Develop cybersecurity teams
Develop a cybersecurity awareness program
Implement continual process improvement
Practice
Protect networks, systems, and data from cyberattacks, failures, and accidents
Implement continual asset and network discovery and mapping
Deploy cybersecurity technologies, processes, and people to protect systems, networks, and data
Build threat landscape awareness
Implement a threat management program
Share information and collaborate with internal and external stakeholders
Posture
Continuously monitor networks and systems
Monitor and enforce policy adherence
Respond to events and incidents
Test IRP/BCP/DRP
Perform risk assessments and simulations
Identify and remediate vulnerabilities
Perform threat hunting
Measure and track cyber resilience
